🕸 Web Exploitation Deep Dive: From SQLi to RCE and Beyond
🐍 Series: Open Deception Framework (ODF) | Arc: 1
Series 1, Blog 1: Chaining multiple weaknesses together.
☠️
Attack Sequencing for Escalation
Attackers rarely settle for exploiting a single flaw. What makes real-world breaches devastating is not the discovery of one vulnerability, but the ability to chain multiple weaknesses together into a sequence of escalating attacks. Think of it as crossing a river: each vulnerability is a stepping stone, and with enough stones lined up, an attacker can reach the full goal – full system compromise.
This blog aligns technical rigor expected at Offensive Security Certified Professional (OSCP) and Certified Professional Penetration Tester (CPPT) levels. The reason is that understanding chained exploitation is not just academic, it’s practical. Many organisations patch obvious issues but miss how minor misconfigurations or overlooked flaws can be linked together into a far greater risk.
We’ll explore why a simple SQL Injection (SQLi) isn’t just about leaking database rows, but can escalate into Remote Code Execution (RCE) if paired with clever pivots. We’ll show how blind XML External Entity Injection (XXE) and Server-Side Request Forgery (SSRF) can quietly tunnel into cloud infrastructure. We’ll unpack the hidden danger of insecure deserialisation and upload bypasses, and finally, we’ll reveal how modern tricks like HTTP/2 smuggling and cache poisoning can weaponise otherwise invisible weaknesses.
By the end, you’ll see why defenders must think in chains, not silos.
⚒️ Tools
- Burp Suite Swiss-army knife for intercepting and tampering with web traffic.
- sqlmap Automated SQLi tool to extract database data.
- wfuzz/ffuf Wordlist brute-forcers to discover hidden endpoints.
- ysoserial Generates Java/.NET payloads for deserialization exploits.
- aws-cli + curl To test SSRF paths to AWS metadata services.
❤️🔥 Topical vulnerabilities
- CVE-2025-32094 HTTP Request Smuggling in Akamai PlatformsAkamai disclosed this HTTP request smuggling vulnerability in March 2025 involving anomalous handling of
OPTIONSrequests withExpect: 100-continueheaders and line folding. Although quickly patched, it exemplifies how subtle protocol misinterpretations can yield chainable exploitation points. - CVE-2025-6442 HTTP Request Smuggling in Ruby WEBrickThis vulnerability affects Ruby’s WEBrick server (
read_headersfunction), allowing attackers to smuggle arbitrary HTTP requests when deployed behind certain proxies. It underscores the importance of consistent header parsing across components. - CVE-2025-53770 / CVE-2025-53771 “ToolShell” Deserialisation Chain in Microsoft SharePointA critical deserialisation vulnerability in SharePoint that, when chained with related flaws (e.g., CVE‑2025‑49704, CVE‑2025‑49706), enables unauthenticated remote code execution. This exploit has been actively weaponised in ransomware campaigns (notably the “ToolShell” chain distributing “Warlock” ransomware), with widespread impact across public- and private-sector infrastructures.
⛓️
Exploit the Full Chain
Experience of web exploitation contributes towards the aid of prevention by revealing how attackers chain seemingly minor flaws into major breaches, thus allowing defenders to harden systems before those weak points are joined together. By strengthening detection through subtle artefacts these techniques leave behind, such as patterns in logs, unusual traffic flows, or malformed requests that traditional monitoring might miss.
Finally, we supports the capture of malicious actors by mapping exploitation behaviour to specific Tactics, Techniques, and Procedures (TTPs), enabling attribution of attacks, reconstructed timelines, and disruption campaigns towards malware delivery, ransomware deployment, phishing infrastructure, zero-day exploitation, and financial fraud operations.
Therefore, we must identify and enumerate attack surfaces, analyse complex vulnerabilities across modern web stacks, and exploit them in controlled lab environments. Core focus areas include: SQLi to RCE pivots, blind XXE to SSRF to metadata exfiltration, insecure deserialisation, polyglot upload bypasses, HTTP/2 smuggling, and cache poisoning.
👻 Ontology: What is this about?
We are dealing with web exploitation as a chain of events. Each bug on its own might look small, but when linked, they form a kill chain that moves an attacker from “outsider” → “insider” → “system owner.”
🔮 Epistemology: How do we know it?
We align material with OSCP and CPPT, reading CVEs, and experimenting with proof-of-concept exploits. This blog simplifies the logic so both beginners and professionals can follow the reasoning.
🏹 Aim
Plan, execute, and document a full chained web exploit, from initial foothold to cloud/host compromise – using professional tools, with clear decision points, mitigations, and reporting.
🧭 Objectives
- Recon and Surface Mapping Inventory of endpoints, parameters, and trust boundaries.
- SQLi → RCE Pivot Move from data access to code execution.
- Blind XXE → SSRF → Cloud Metadata Exfiltration Use XML parser weakness to trigger internal requests and read cloud creds.
- Insecure Deserialization Gadget Exploitation Identify serialisation format & exploit a gadget chain for RCE.
- Polyglot Upload Bypass → Code Execution / File Placement Bypass content-type/extension checks to land executable or controlled file.
- HTTP/2 Request Smuggling → Cache Poisoning Desync front/back ends to inject a hidden request, then poison cache keys.
- Privilege Escalation & Lateral/Vertical Movement Expand from web tier to system or cloud role with higher privileges.
- Defense-in-Depth & Remediation Mapping Map each exploit to concrete fixes/controls.
- Operational Reporting & Diagramming Consultant-grade report and visual kill chain.
Think of it as the difference between rattling a locked door and sitting inside the control room with every master key, security override, and CCTV feed at your fingertips.
🪄
Tactical Map
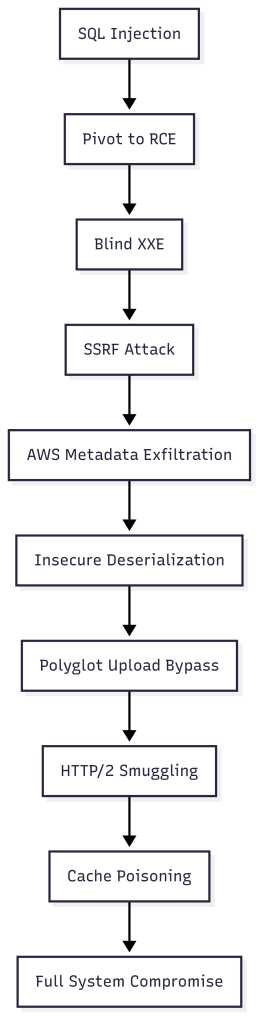
🔥The endgame is possession without presence.