🕸 Advanced Reconnaissance and Enumeration
🐍 Series: Open Deception Framework (ODF) | Arc: 0
Series 1, Blog 0: An Introduction to operation – mapping the terrain.
🧭
Mapping Terrain
In cybersecurity, reconnaissance (“recon”) is the crucial first stage in any penetration test or attack simulation. It’s the art and science of finding every possible target surface before you attempt to exploit it. If hacking were a heist movie, recon is the part where the crew studies blueprints, patrol patterns, and security cameras – but here, the “blueprints” are network maps, domain records, and system fingerprints.
Modern recon is layered – meaning you don’t just run one scan and call it a day. You stack multiple tools and techniques so that each pass reveals more detail. For example:
- Masscan A lightning-fast port scanner that can check millions of IP addresses in minutes. Think of it as a radar sweep for every “door” (network port) in range.
- Nmap with NSE scripts Nmap is slower but more thorough, and its Nmap Scripting Engine can automatically test for known vulnerabilities once Masscan has found open ports.
- CeWL A “Custom Word List generator” that crawls a website to collect keywords, names, and phrases. These are later used for targeted password guessing.
- Amass An advanced tool for mapping domain infrastructure and discovering hidden or forgotten subdomains that could be exploited.
- Kerberos/LDAP reconnaissance Gathering details from authentication systems and directory services that may reveal weak accounts or outdated machines.
- SOCKS proxy pivoting Routing your traffic through a compromised host to scan internal systems that are normally unreachable.
The reason this matters? Advanced recon can identify serious vulnerabilities before attackers do. For instance:
- CVE-2024-27198 TeamCity authentication bypass.
- CVE-2024-4577 PHP CGI injection that allows remote code execution.
- CVE-2023-4966 Citrix leak exposing sensitive session data.
All three could be detected in a well-structured recon pipeline, potentially saving an organisation from catastrophic breach.
Upskilling in advanced recon means developing the ability to see the entire chessboard before the first move whether you’re defending a network or ethically testing one.
🗝️
Offensive Mindedness
Advanced recon and enumeration isn’t about “hacking” for its own sake – it’s about understanding the digital terrain before you step into it. In the physical world, special forces never charge into an unknown building without blueprints, surveillance photos, and intel from locals. In cyberspace, recon is that intel.
Our position in this training is unapologetically offensive-minded. Not because we’re promoting attacks, but because defensive thinking alone leaves blind spots. Modern cyber attackers are highly organised, methodical, and increasingly automated. If security professionals only study the defence playbook, they’ll always be a step behind.
Let’s lean into ethical offensive security, using the same tools and tactics that real attackers use, but in a controlled, legal environment. It’s a safe sandbox to learn the craft, so that when you return to the real world, you can recognise the earliest signs of trouble and respond before an incident snowballs.
The aim is threefold:
- Fluency in advanced reconnaissance pipelines Not just knowing tool commands, but understanding why to use one over another and how to combine them for layered insight.
- Proficiency in pivoted and stealth techniques Learning to gather intel even when direct access is blocked, by relaying through compromised or approved footholds.
- Recognition of high-value vulnerabilities in context Spotting how a seemingly minor misconfiguration can chain into a critical breach.
Think of it as the difference between seeing a building from the street… and having the blueprints, keycard schematics, and guard shift schedules in your pocket.
🪄
Tactical Map
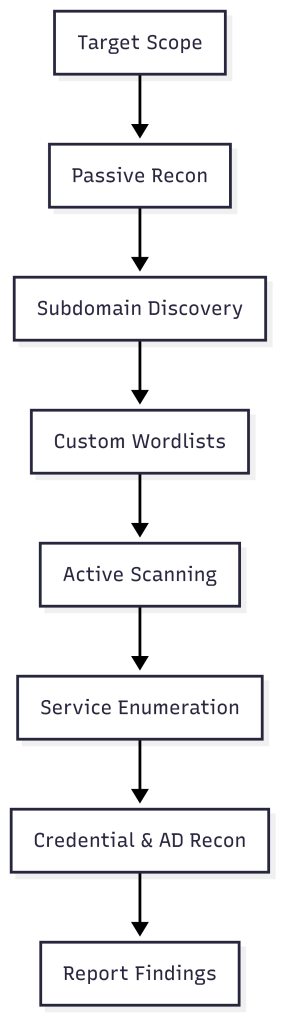
🔥 The best recon is a ghost – it learns without being seen, and vanishes without a trace.