🕸 Linux Privilege Escalation Mastery
🐍 Series: Open Deception Framework (ODF) | Arc: 2
Series 1, Blog 2: From SUID chaining to container escapes.
🐧
From Foothold to Full Kernel
On Linux systems, the first foothold is rarely the last word. More often, an attacker arrives as a low-privilege user, a shell with boundaries. The challenge, and the true test of skill, is to turn that fragment of access into complete control. This process, known as privilege escalation, is not just a set of tricks. It is an arc of mastery, one that mirrors the professional journey from OSCP to OSEE.
At the Offensive Security Certified Professional (OSCP) level, the emphasis is on practical escalation: finding Set User ID (SUID) binaries, poisoning environment variables, and exploiting simple misconfigurations to move from user to root. These are the fundamentals – the foothold-to-root skills every penetration tester must demonstrate.
Progressing into the Certified Red Team Operator (CRTO) mindset, privilege escalation becomes tradecraft. It is no longer about a one-off root shell, but about persistence, stealth, and chaining attacks in enterprise-like environments. Here, systemd misconfigurations and container breakout scenarios come into play, teaching operators how adversaries think when building long-term access.
The GIAC Exploit Researcher (GXPN) stage represents a shift into exploit research. It is the ability to take a proof-of-concept CVE, adapt it to real-world constraints, and weaponise it into a functional local exploit. This is where escalation transcends scripts and becomes engineering.
Finally, at the Offensive Security Exploitation Expert (OSEE) tier, privilege escalation reaches its most advanced form: bypassing hardened controls like AppArmor and SELinux, mastering kernel-level exploitation, and proving capability against fully patched systems. This is the pinnacle – the difference between imitating attackers and truly understanding the mechanics of system compromise.
This blog walks through that full arc. Each stage is not just a technique, but a stepping stone in professional growth, towards foresight to recognise escalation in action and the mastery to prevent it before it takes hold.
⚒️ Tools
- LinPEAS Automated privesc enumeration (SUID, capabilities, configs).
- LES (Linux Exploit Suggester) Suggests kernel exploits by version.
- Pspy Process monitoring without root.
- Strace / Ltrace Syscall tracing, useful for SUID analysis.
- GTFOBins Curated list of SUID-exploitable binaries.
- Find & Grep Manual discovery:
find / -perm -4000 2>/dev/null. - GDB / pwntools Debugging and exploit dev (GXPN/OSEE tier).
❤️🔥 Topical vulnerabilities
- CVE-2025-32462 Policy-Check Flaw in sudo
This vulnerability allows unprivileged users to bypass host-based restrictions in the sudoers policy and run commands as root without needing full sudo permissions. It affects versions up to 1.9.17p1 on most Linux and macOS systems. - CVE-2025-32463 chroot to root flaw in sudo
A critical bug that lets local users exploit the--chrootoption in sudo. By placing malicious configuration files or shared libraries, attackers can gain root execution—demonstrating how misconfigurations lead directly to privilege escalation. - CVE-2025-6019 libblockdev / udisks2 Polkit escalation
Here, a local user with console privileges abuses the libblockdev and udisks2 interplay to mount a deliberately crafted XFS image without safety flags (nosuid,nodev). This allows execution of a SUID-root shell and full privilege escalation.
⛓️
Connecting Intrusion to Compromise
Privilege escalation is not just a technical trick – it’s a window into how offenders consolidate control over compromised systems. Criminals rarely gain “root” in one step. Instead, they exploit small weaknesses: a misconfigured binary, a service running with the wrong permissions, or a poorly secured container. On their own, these flaws look insignificant. But chained together, they allow an attacker to climb from a low-level account to complete control of a server, and from there, potentially into wider networks.
For investigators, understanding this process is vital. It reveals how a simple intrusion escalates into full system compromise, helps identify digital traces attackers leave behind, and shows where defensive gaps could have been closed earlier. This knowledge equips us to:
- Spot escalation attempts during live incident response.
- Trace adversary movement across compromised systems.
- Recognise tampering or hidden data using elevated privileges.
- Mapping how small errors were weaponised into major breaches.
By studying Linux privilege escalation as both science (vulnerability mapping) and art (the attacker’s rhythm), we can move beyond reactive investigation and towards proactive foresight – identifying escalation chains before they allow offenders to gain dominance.
🔮 Ontology
We treat Linux privilege escalation as a chain of misconfigurations, binaries, and kernel flaws. Each weakness may look harmless in isolation, but when chained, they allow attackers to move from local user → root → host escape.
👻 Aim
Master Linux privilege escalation by exploiting misconfigs, chaining CVEs, and bypassing controls for detection and defence.
🧭 Objectives
- SUID discovery, PATH hijacking, and GTFOBins exploitation.
- Learn to chain privesc methods for stealth and persistence in ops.
- Weaponise kernel CVEs and research misconfigurations.
- Develop bypasses against hardened systems (AppArmor, SELinux, containers).
Think of it as the difference between peering through a keyhole and commanding the entire building from the root console.
🪄
Tactical Map
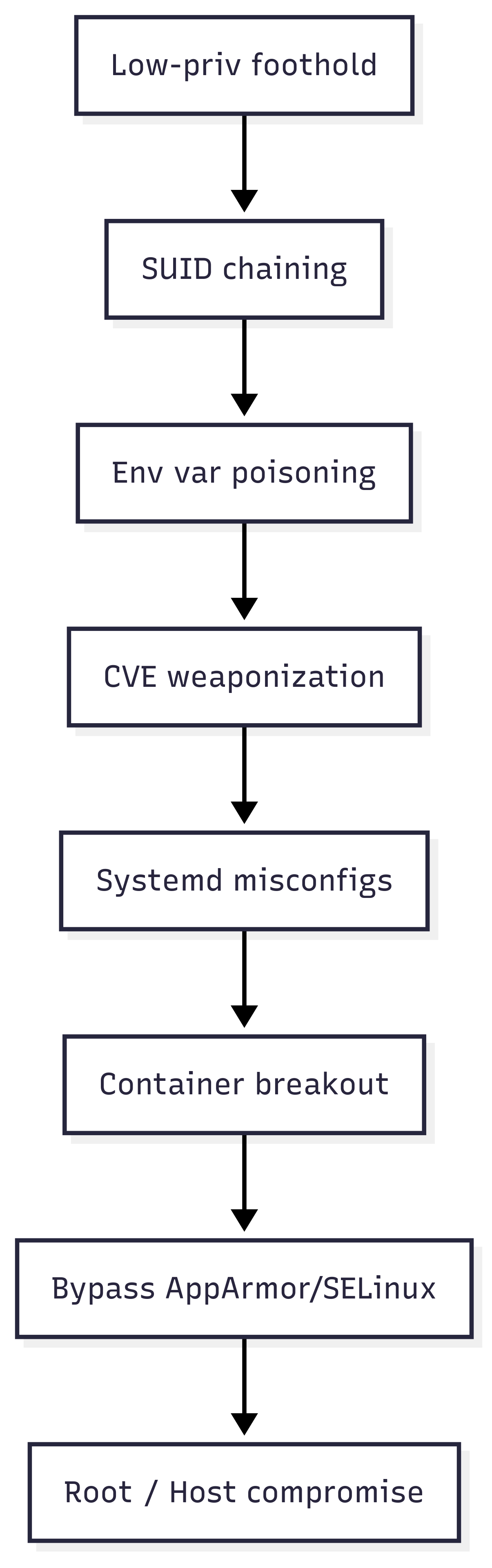
🔥The endgame is escalation without exposure.